

Information systems offer many benefits for companies in terms of efficiency and organization. Yet, some companies see the institution of new technology as a hassle, making electronic information protection just another roadblock. However, with the emergence of the Health Information Trust Alliance (HITRUST) , information protection has become more manageable, particularly with the creation of the Common Security Framework (CSF).
There are various factors that businesses should be aware of to best meet HITRUST CSF requirements . Read on to find out what the requirements are to become HITRUST certified.
HITRUST began in 2007 as a non-profit entity seeking to help healthcare providers and insurers better protect their electronic personal health information (ePHI) and systems. HITRUST develops standards, frameworks, and methodologies related to information security, as well as providing training and tools for small and large businesses. The CSF helps entities identify and analyze systems to better address security threats . As of 2018, 81 percent of US hospitals and 83 percent of US health plans adopted the CSF. Even if you aren’t in the healthcare industry, HITRUST offers many resources and services for risk management.
The HITRUST CSF Advisory Council reviews and updates the CSF as the healthcare industry changes. More recently, the council has focused on expanding the applicability of the CSF to other industries, particularly those that lack compliance programs . The current version of the CSF is v9.2 . The following groups compose the Council:
The diversity of the council means the CSF guidelines do not remain stagnant but shift and expand as new threats emerge . The independent nature of the council also increases the objectivity and ensures any changes to HITRUST’s goals benefit the industries involved.
In concert with the Advisory Council, the Research Advisory Council (RAC) helps keep the CSF from becoming obsolete. The RAC focuses on emerging technologies that may affect security standards and threats in the future. For example, blockchain and the Internet of Things (IoT) are two topics currently under review. In order to keep the Council relevant, subject matter experts from outside HITRUST make up the RAC, either from the industry or academia.

The CSF brings together the numerous privacy and regulatory standards companies face into a single platform and process. Rather than attempting to simultaneously complete many certifications at once, the CSF consolidates state and federal standards. As noted above, the newest version of HITRUST also integrates international regulations, like the GDPR , into the certification process. HITRUST enables companies of various sizes and industries to satisfy security requirements by following the CSF risk-based, multi-level approach to security. The flexibility the CSF provides makes it versatile, although it initially focused on the healthcare industry. Moreover, the CSF is ideal for small businesses due to its customizable characteristics. The best way to use the CSF is to use it in conjunction with HITRUST’s web-based tool called MyCSF.
The CSF includes 14 control categories, 46 control objectives, and 149 controls. For each control, there are 3 levels. However, not all of the objectives and controls are applied to every company that chooses to start the certification process . Prior to starting the in-depth process, every company must choose which type of assessment to conduct. There are five options:
When choosing a type of assessment, another consideration is what compliance guidelines you wish to fulfill. HITRUST certification , depending on the assessment and plan chosen, can fulfill HIPAA , PCI DSS , NIST 800-53, NIST Cybersecurity Framework, and COBIT.
After determining the end goal and selecting an assessment type, you will use the 14 control categories during the risk assessment, which is part of any of the above assessments. The difference lies in the comprehensiveness and scope of the assessment. Below are the 14 control categories that, in addition to compliance, help companies address cybersecurity with a holistic approach.
Prior to HITRUST, companies typically confirmed their HIPAA compliance through signed or verbal agreements. However, that process wasn’t reliable or standardized, making it difficult to enforce HIPAA regulations . Another option allowed SOC reports or attestation documentation to confirm compliance. But again, that process provided little regularity and resulted in ambiguity. The HITRUST method provides a central consolidated process for confirming compliance.
Prior to beginning the validation process, companies must complete several preparatory steps. First, companies need to complete a self-assessment, which includes a thorough risk analysis. Risk analysis is key because it will determine the implementation level of controls later down the road. Next, a CSF assessor will analyze the self-assessment results and the remediation steps taken on the part of the company. Finally, the CSF assessor will review the performance of controls and, if satisfactory, issue a letter of certification. The following diagram depicts the CSF certification process.
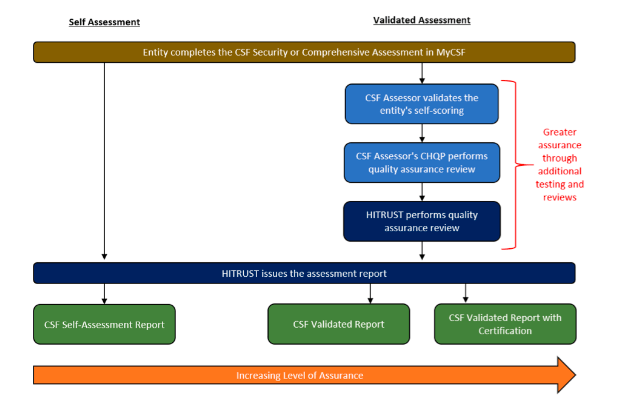
CSF certification takes time, commitment, and a certain level of patience. The process will not happen overnight, and depending on the scope could take anywhere from three to four months .
Scope is the main determinant of how long the certification process will take. For example, a company can choose to certify one department, multiple departments, or the entire company. For small businesses, complete certification may be possible, but for larger businesses, it is recommended to limit the scope of assessment by department.
Use the following steps to begin planning your HITRUST certification:
A self-assessment covers organizational, geographic, regulatory, and system risks. Using CSF methodologies and the MyCSF tool, companies will answer a questionnaire to identify the scope necessary for their assessment. After answering the questions, companies will receive a list of controls that should be utilized. For each control, companies will enter responses (e.g., is the control used and to what extent). Then, the MyCSF tool will rank a company’s maturity level in terms of its current policies/procedures. A company may fall into one of five PRISMA-based maturity levels: non-compliant (0 %), somewhat compliant (25 %), partially compliant (50 %), mostly compliant (75 %), fully compliant (100 %).
For each control, the following questions will likely be asked:
After a maturity level is determined and related questions answered, the MyCSF tool generates a report. While this report does not serve as a certification, it can be a useful report for business partners who request information on security measures in place. The report will also be beneficial if a company chooses to go all the way and achieve HITRUST CSF certification .
A CSF validator has two goals: verify that the self-assessment scores were accurate and ensure that remediation efforts were implemented. In order to fulfill these goals, a validator will not only review documents but also conduct an on-site walkthrough. The assessor will interview relevant personnel, inspect written policies, observe controls in action, perform control testing, review control metrics (in terms of how success is measured), and review the reports generated by monitoring mechanisms. NIST’s Special Publication 800-115 , Technical Guide to Information Security Testing and Assessment underlies HITRUST’s validation process.
The assessor takes into account the environment of each company and develops a unique test plan for the validation process. The test plan is linked to the PRISMA maturity levels and the related illustrative procedures. Likewise, the assessor will outline samplings and working papers. Working papers show the assessor’s agreement or denial of a company’s self-scoring from the self-assessment phase while the sampling documents outline what systems or procedures will be tested in the presence of the assessor. The sampling and work paper documents go hand in hand as the samplings help determine if the scoring was correct.
According to the National Institute of Standards and Technology, the PRISMA review model looks at policy, procedures, implementation, testing, and integration when determining IT security maturity. These factors influence the HITRUST compliance process. Each of the above categories builds upon one another, meaning a higher level of maturity is dependant on all five areas being addressed.
IT Security Maturity Level 1: Policies
Fulfilling this policy level relies on documentation, organization, and administrative tasks. For example, documented security policies with guidelines for all company employees should be distributed and updated on a regular basis. Likewise, an assessment/risk monitoring cycle, IT management/responsibility policy, and disciplinary policy should also be established.
IT Security Maturity Level 2: Procedures
Once policies are in place, their procedural documents should explain the process for implementing the required security controls. Procedures should cover how, when, and who will implement the control, as well as what system the control affects. Furthermore, procedures should identify the IT responsibilities the controls will require and how system users, personnel, and security administrators should conduct themselves when interacting with the system.
IT Security Maturity Level 3: Implementation
Implementation follows through on the preparation and documentation phases. Implementation requires distributing the policies and procedures to employees, making sure the requirements and expected behavior stipulation are clear. Then, companies should provide training. For example, train employees on how to identify a malicious email . NIST encourages companies to establish consistency rather than implementing procedures in an ad hoc style. Finally, this stage sets the wheels rolling for the testing stage by prepping systems and running diagnostics.
IT Security Maturity Level 4: Testing
Although the previous level begins the testing process, the PRISMA system sets aside a whole level for testing because of its vital importance in maintaining data security . Testing verifies that controls are functioning as expected and that the level of security adequately satisfies standard requirements. Self-assessments and remediation also fall under the testing phase. Any security incidents whether within your company or within the industry should be considered.
IT Security Maturity Level 5: Integration
Integration focuses on bringing all the above levels together and making sure departments and policies do not remain stagnant after initial certification or assessment. Rather, companies should continue making security decisions based on cost, risk, and mission impact. Furthermore, companies should evolve as they grow in size or as resources change, always remembering to keep security standards in mind when shaping new IT security goals and policies.

If you’re interested in HITRUST certification , the first step is to contact HITRUST directly as well as conduct research on what type of certification you need. What level of security do your vendors or business partners require? Next, get in touch with a HITRUST assessor . HITRUST will help establish a relationship between your company and an approved assessment firm. Lastly, begin researching the CSF and how it fits with your company’s needs and goals.
Compliance today is essential to business, whether it be for consumer peace of mind or to strengthen business partnerships. HITRUST continues to research and expand its CSF options, with new requirements being added as the threat landscape evolves. To learn more about HITRUST certification requirements or to begin the assessment process, contact RSI Security today .
Assess where your organization currently stands with being HITRUST compliant by completing this checklist. Upon filling out this brief form you will receive the checklist via email.